
ADCS – Create a Template for Remote Desktop Certificate via (AD CS)
10 November 2019We begin by opening the CA Management Console, right-clicking the certificate templates and selecting Manage.
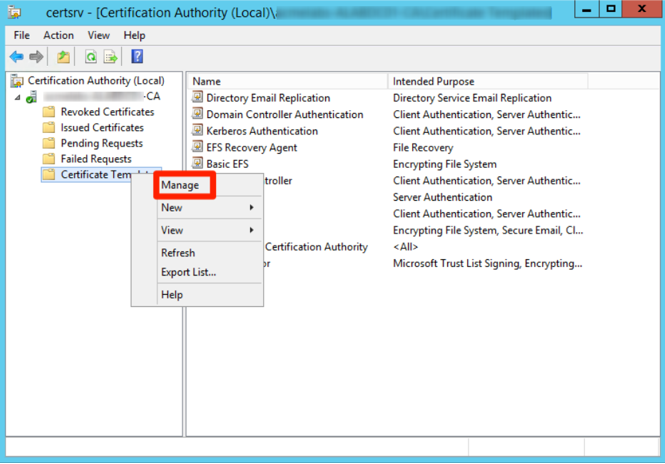
This will open a model management console. Scroll down and select Computer Model and right-click on it by selecting Duplicate Template.
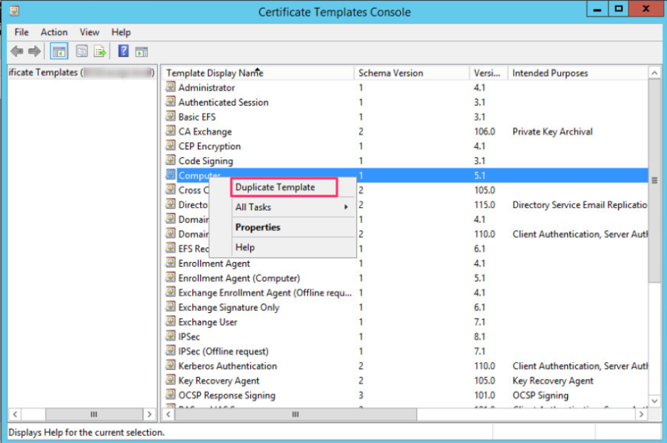
This will open a model management console. Scroll down and select Computer Model and right-click on it by selecting Duplicate Template.
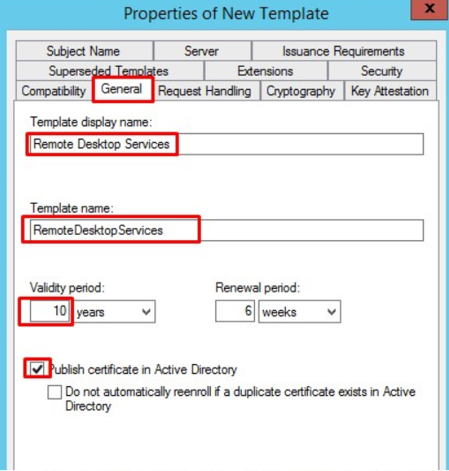
In the certificate property window for the new template, we access the General tab and define a display name and a template name. I recommend using the same and without spaces.
We need to make sure that the appropriate extensions are set for it to work on both Windows and other platforms for TLS. On the Extensions tab, click Edit to edit the extensions of the certificate that will be issued.
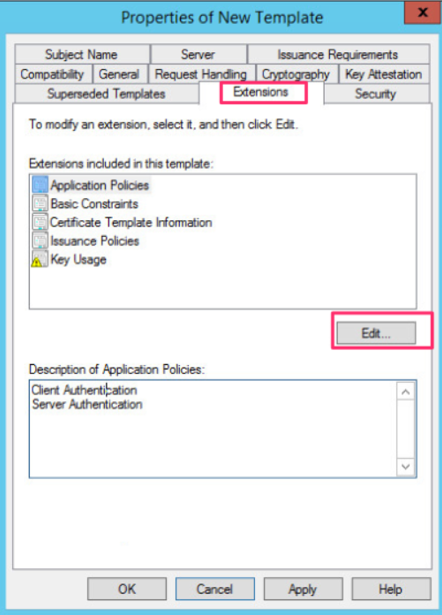
We will select the client authentication and click Remove.
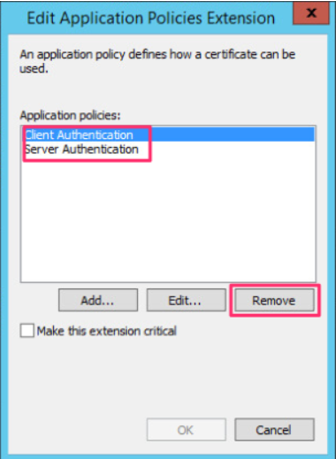
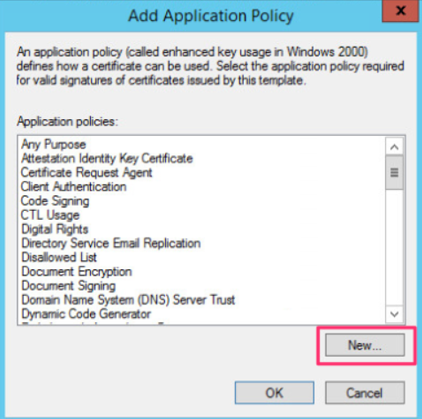
After you have removed the client authentication policy, click Add Now and in the window that appears, click New to create a new policy specific to using TLS RDP.
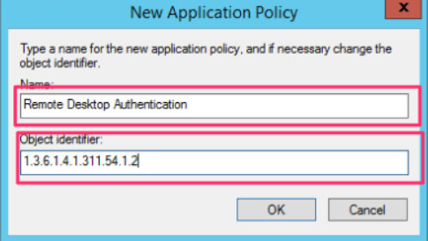
We provide a name for the strategy. In the example, I give it the name Remote Desktop Authentication and an object identifier of 1.3.6.1.4.1.311.54.1.2. This certificate identifies the certificate as being used to authenticate an RDP server.
On the Security tab, we need to identify the systems that can register using this template. Domain computers are already present and with the Registration permission, but if you also plan to enable RDP on the domain controllers, add the domain controller group and make sure that the Registration permission is selected.
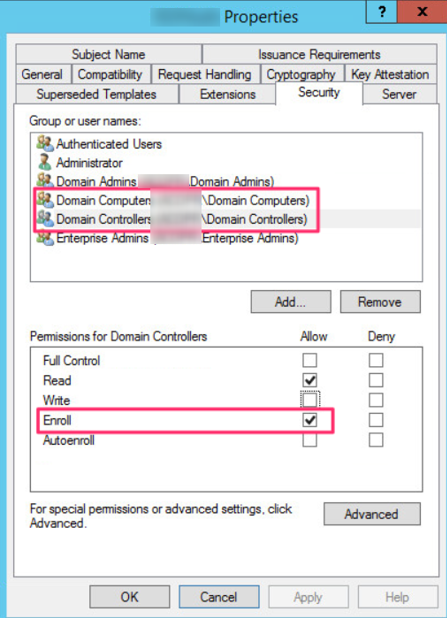
If you have computers that can not register using the certificate template, a quick way to identify it is to search the event viewer in the Windows system log for events with ID 1064 the TerminaServices-RemoteConnectionManager source.
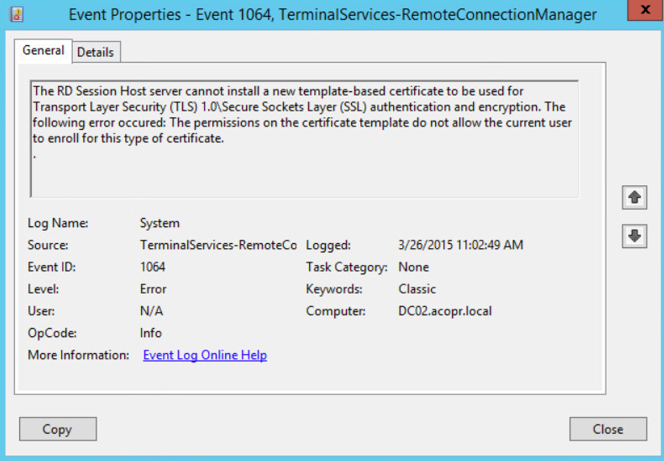
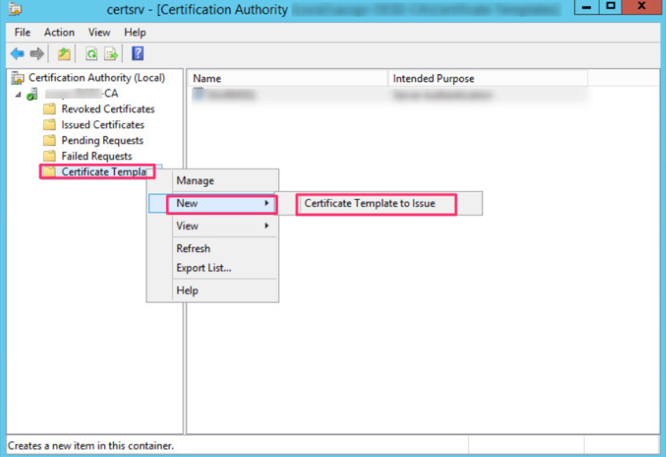
To make the certificate available for enrollment on computers, go to the CA Management Console and select under the certificate authority’s CA template, right-click and select New -> Certificate template to be issued.
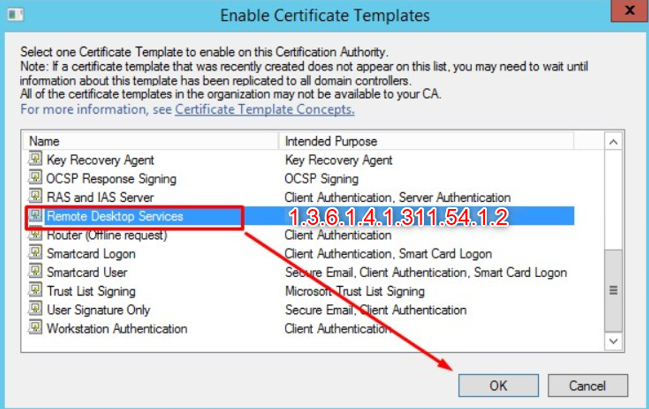
In the Enable Certificate Templates window, select the certificate template that you just created, and then click OK.
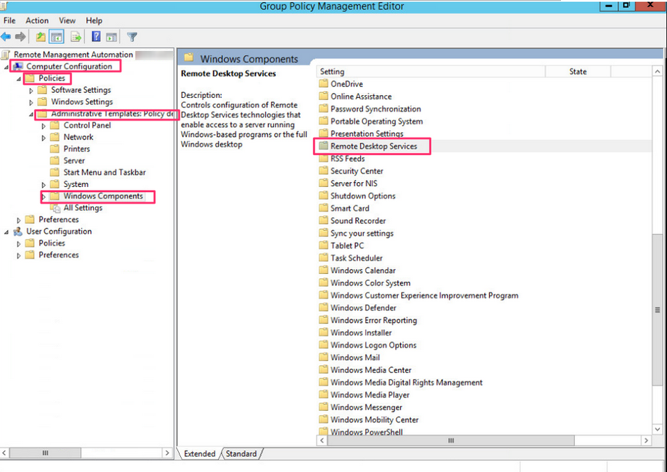
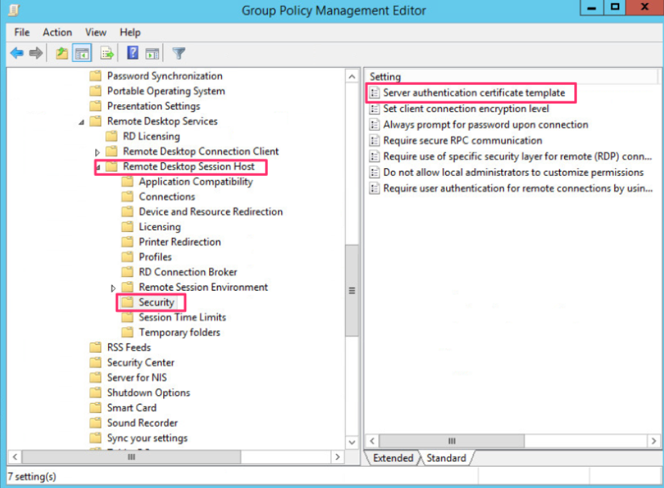
We now need to configure a GPO that will be bound to the Active Directory container where the hosts for which we want to be able to request the certificate template. We begin by creating or selecting an existing GPO and modifying it. In the GPO, select Computer Configuration -> Policies -> Administrative Template -> Windows Components -> Remote Desktop Services -> Desktop Remote Host -> Security and select Server authentication certificate template.
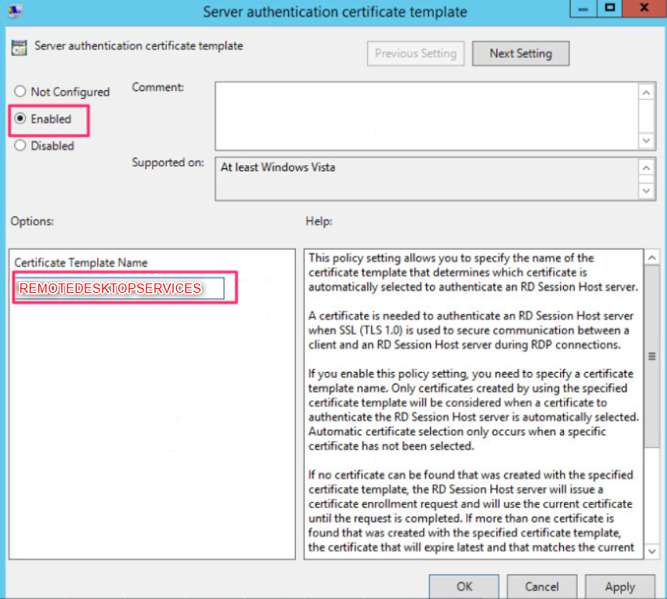
On the setting, click Enable and under Certificate Template Name, enter the certificate template name that we made available for registration and click OK.
Thank you for reading this post, don't forget to subscribe!
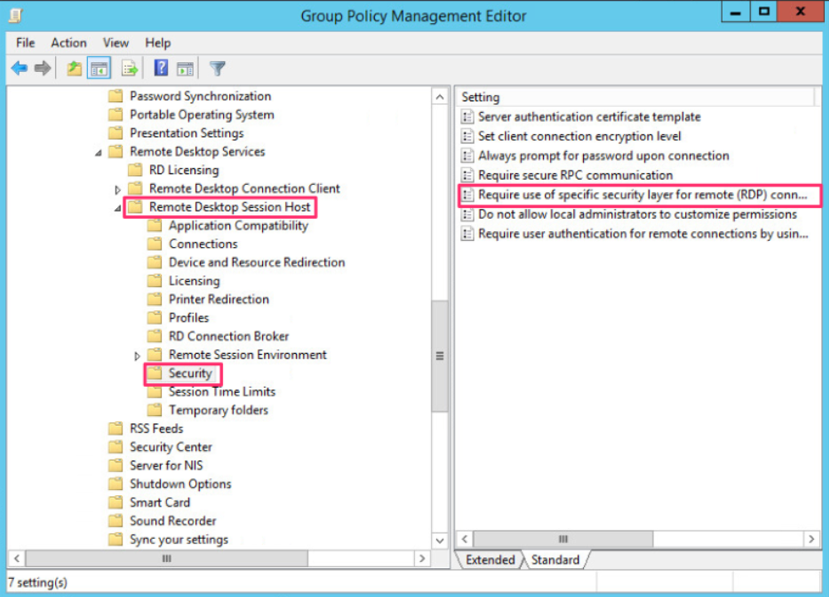
We click Enable and Security Layer, select SSL (TLS 1.0) from the drop-down list, and click OK.
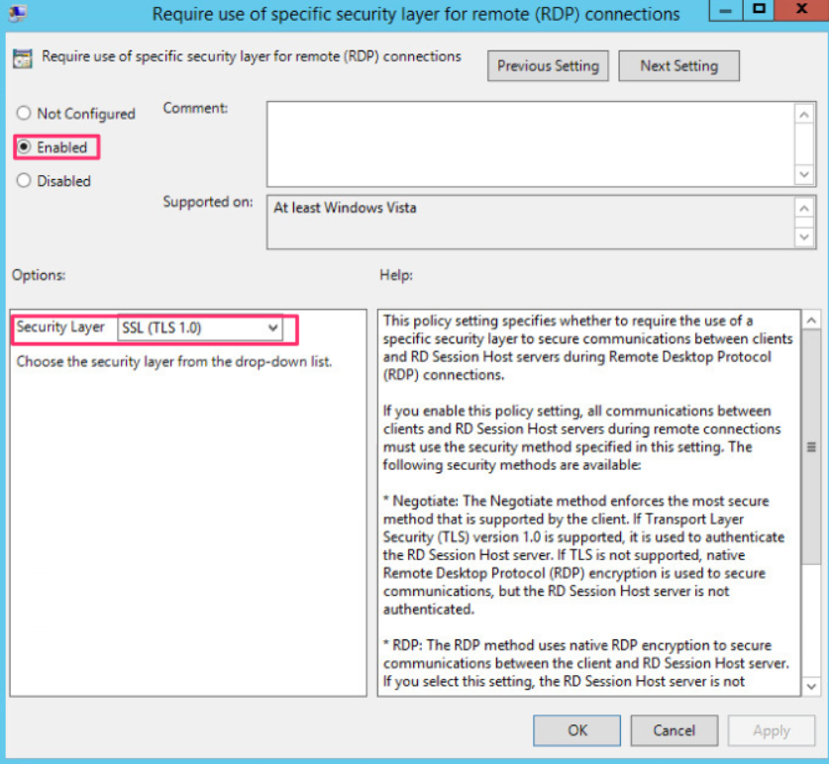
In security settings, I would also recommend enabling NLA, they will break most of the public RDP forcing tools. Select Require user authentication for remote connections by using Network Level Authentication and double-click it. On the property screen, select Enable and click OK.
Also, because we do not want users to simply accept and trust connections because it goes against all of these parameters, we make sure that clients always validate the server certificate. We select Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Remote Desktop Settings -> Remote Desktop Connection Client. Double-click Authentication for Client. Select Enable and set the option to Warn me if authentication fails.
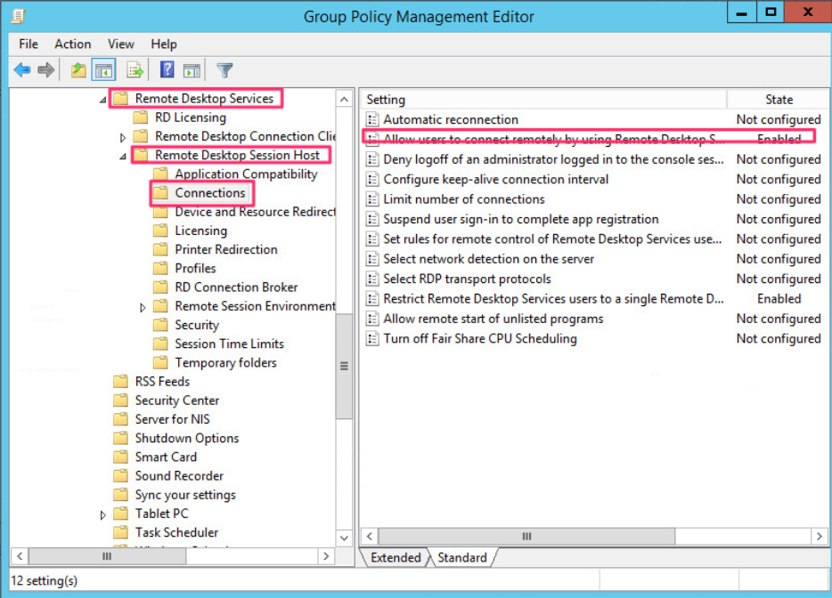
If Remote Desktop is not enabled on another GPO, you must access Connections under Remote Desktop Session Host and enable Allow users to connect remotely by using Remote Desktop Service.
Views: 27021


